Trending Now
- “I will soon make an announcement regarding a statewide tour across Tamil Nadu.” – O. Panneerselvam.
- Vatsala, Asia’s oldest elephant, has passed away at Panna Tiger Reserve; social activists mourn the death of this elephant, which lived for over 100 years.
- “The U.S. Govt earned ₹8 lakh crore this year through increased tariffs on foreign goods.” – U.S President Donald Trump.
- World No.1 Aryna Sabalenka has advanced to the semifinals in the Women’s Singles category at Wimbledon Tennis.
Coimbatore
App permissions pose security, data privacy risks
![]() October 24, 2018
October 24, 2018
Millions of Smartphone users in India are vulnerable to risking data privacy. And in this era where personal information is harvested at such a huge scale, it can be weaponised to sway opinion right from buying clothes or influencing your decision during elections, according to security experts. They have called for much wider attention when it comes to mobile security.
Substantiating this scare comes the latest report by The Wall Street Journal. It says cheap and affordable smartphones in developing countries, including India, come with apps that sell user data. Companies like Xiaomi, Huawei and Sony have been listed as device partners for firms to access user data on smartphones. Facebook was caught this year in the biggest data breaching scandal ever.
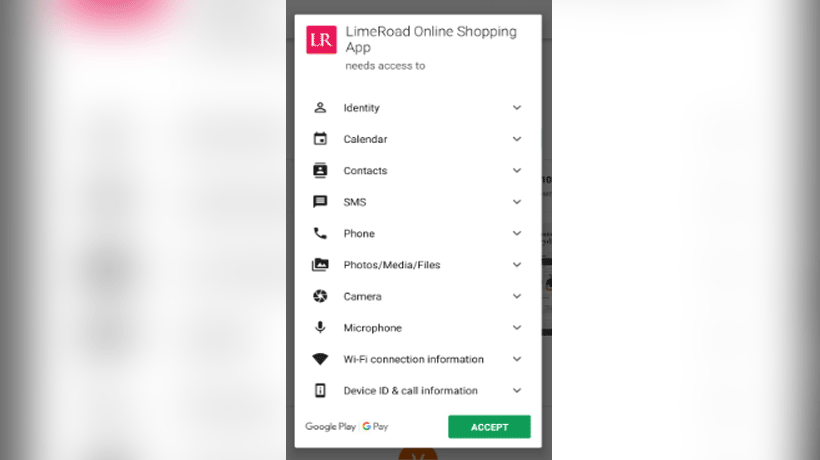
Android permissions are software developer’s best friend, but mobile user’s worst enemy, experts note. Apps from reputable companies and developers are seeking dangerous permissions which include access to microphones to record audio, call logs, calendar, SMS, storage and sharing location information. They are said to be gathering details about emails and social media accounts.
“It’s a security nightmare. When the loss is minimum we are not bothered and choose to ignore the problem. Only when the loss is monetary people pay attention to privacy and security issues.” says PSG College of Technology professor A Soundararajan.
Some apps like flashlight could be an easy conduit for malware which can compromise the security of the phone. Hackers can misuse details in various ways. Information such as bank account details, credit card data can be stolen or misused and passwords can be changed to get access to confidential and private data. Malicious code can be sent on the phone that allows them to read messages, and balance amount can be used to make a call. Worse still, this call can be made by someone else to cause harm to the reputation of high profile people.
Many apps use voluminous terms of agreement to seek permission to get access to everything. “E-commerce apps will have a rationale, explanation and reason behind wanting access to your phone. The best thing is to see if we really require the app. One can go to the website rather than downloading the app. Both suffice the purpose. Do not keep your bank details in your phone,” said a security expert here.
“Download app from a trustworthy developer. If you are suspicious of malware, don’t download the app. Understand why the app needs so many permissions, they are listed in the Play Store along with reasons for each permission request,” he points out.
“Upgrade your phone on a regular basis, download antivirus on your phone, PC or laptop, and switch off GPS and internet when not in use. However, because of Jio, it seems everyone is hooked on to the net,” adds Soundararajan.
According to research firm eMarketer, with the entry of Reliance Jio, data costs have become affordable to just about anyone who can buy a smartphone. This means millions of excited first-time users of smartphones with a suboptimal understanding of security protocols, including what is safe to click and what might not be, will fall prey. If there is a feature in the app just do not install the app and find an alternative that os more transparent, is the advice.
Besides the violation of an individual’s data privacy, there is also a matter of national security. Raghu Raman, former CEO of the National Intelligence Grid, who now serves as group president for risk, security and new ventures at Reliance Industries, says the problem goes well beyond the mobile OS that is used.
“We tend to forget that the base hardware isn’t made by us, nor is much of the software, including the anti-malware tools meant to keep us safe,” he says.
Raghu does not think it is a great idea for the government to use the telecom gear we buy from a potentially hostile country, even if it is vetted by a friendly country. “We’ll just have two pieces of malware to contend with in that case, rather than one,” he adds.